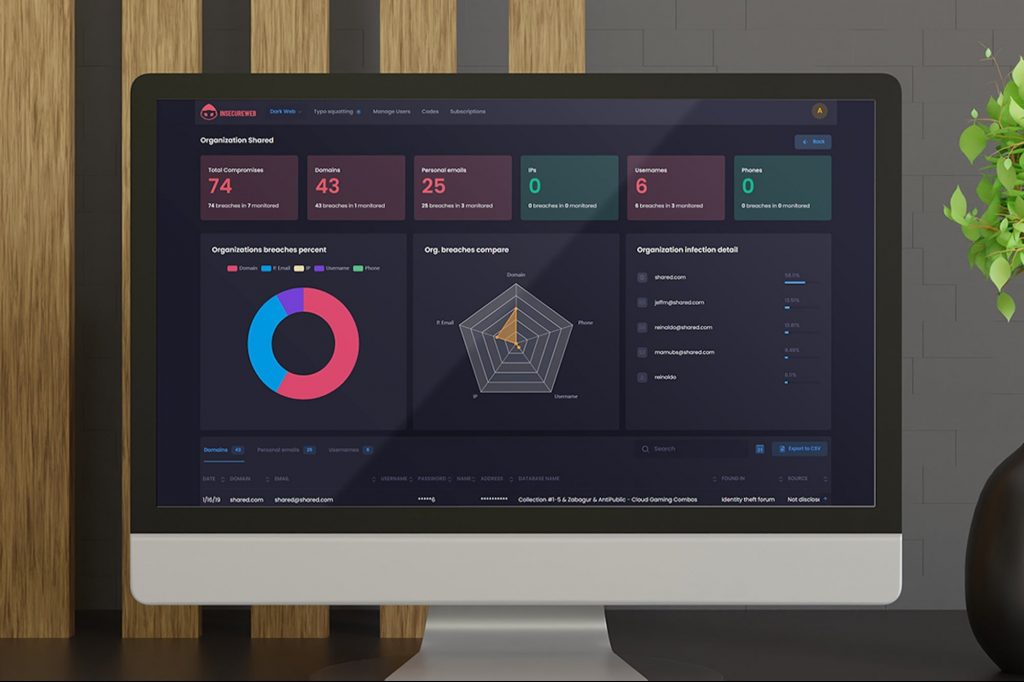
TorZon Darkweb Encourages Safe Exploration of Digital Spaces
The digital world continues to expand, offering both opportunities and risks for those who venture into its depths. While some parts of the internet are designed for general use, others remain more obscure, often referred to as the dark web. Navigating these spaces can be a daunting task, as they are frequently associated with illegal activities and unsafe practices. However, this hidden part of the web also has a legitimate side that can provide valuable insights and privacy. It is crucial for individuals interested in exploring these spaces to approach them with caution, awareness, and the proper tools. When exploring the dark web, the first step is to ensure that your digital safety is a priority. It is essential to use encrypted and secure browsing methods that mask your identity and protect your data. Special software, such as anonymous browsers, allows users to access these spaces without revealing personal information or leaving behind a traceable footprint. Understanding the potential dangers is key to ensuring a safe and productive experience.
Anonymity plays a significant role in maintaining security on the dark web from TorZon link. Whether browsing, communicating, or exchanging information, remaining anonymous shields users from being tracked or identified. This level of privacy is often the main reason why many individuals explore the dark web, as it offers a space where sensitive matters, such as political activism, research, and personal privacy, can be discussed freely. However, while anonymity is beneficial, it should not be taken for granted. Users should still take proactive steps to protect their devices from cyber threats. In addition to using encrypted connections and remaining anonymous, it is important to navigate the dark web with a critical eye. Many resources and services available on these platforms may seem legitimate at first glance but can be fraudulent or dangerous. Scams are unfortunately prevalent in such spaces, and individuals should be cautious before trusting unknown sources. Engaging only with verified communities or services can reduce the risk of falling victim to fraud or malicious activities.
Verification methods can include recommendations from trusted sources or clear signs of a service’s reputation. It is also essential to acknowledge that not all content on the dark web is harmful. While some sections may be involved in illegal activities, there are many others where individuals share resources for academic research, technological advancements, or humanitarian efforts. The dark web can serve as an important platform for those seeking freedom of expression in countries with strict censorship or surveillance. For example, journalists, whistleblowers, and activists often rely on secure communication channels to exchange vital information without fear of reprisal. However, as with any part of the internet, users should approach the dark web with a mindset of responsibility. Engaging with the digital world in a way that respects both legal and ethical boundaries is crucial. Exploring these spaces should not be seen as a way to escape rules or engage in malicious activity, but rather as an opportunity to seek privacy and access information that might not be available through mainstream channels.